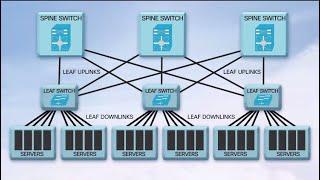
Connected medical devices cannot protect themselves. Like many IoT devices, they either lack the system resources to run any significant security capabilities, or they weren’t designed with security in mind. Regardless, they have a critical role to play in healthcare delivery and must be protected in a way that allows them to perform their functions unimpeded.
Medical devices should be segmented from the rest of the network with only minimal traffic from the device to anything outside its segment. Unlike industrial devices, an exploited device should be immediately quarantined. Medical devices have a direct 1:1 correlation between device and patient at the time of use, and loss of control or interference with that device could have a direct, negative impact on the patient.
Learn how IoT Threat Defense can be applied in Healthcare to create a defense-in-depth architecture that protects clinical devices and is an enabler for our customers’ IoT journey every step of the way.
http://cs.co/60598aGqt
Medical devices should be segmented from the rest of the network with only minimal traffic from the device to anything outside its segment. Unlike industrial devices, an exploited device should be immediately quarantined. Medical devices have a direct 1:1 correlation between device and patient at the time of use, and loss of control or interference with that device could have a direct, negative impact on the patient.
Learn how IoT Threat Defense can be applied in Healthcare to create a defense-in-depth architecture that protects clinical devices and is an enabler for our customers’ IoT journey every step of the way.
http://cs.co/60598aGqt
- Category
- Cisco Systems
Be the first to comment