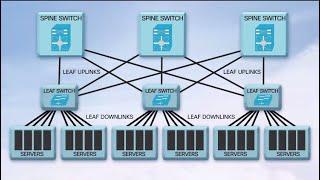
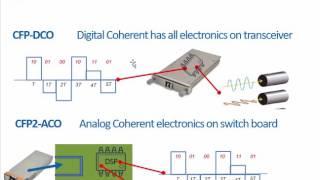
The attack surface exposed by proprietary layer 2 protocols contains hidden bugs that have severe implications to the security of the devices that use them, as well as the networks they belong to. We discovered 5 such zero-day vulnerabilities....
By: Barak Hadad & Ben Seri
Full Abstract & Presentation Materials:
https://www.blackhat.com/asia-20/briefings/schedule/#cdpwn-taking-over-millions-of-enterprise-things-with-layer--zero-days-18806
By: Barak Hadad & Ben Seri
Full Abstract & Presentation Materials:
https://www.blackhat.com/asia-20/briefings/schedule/#cdpwn-taking-over-millions-of-enterprise-things-with-layer--zero-days-18806
- Category
- Routers and Switches
Be the first to comment