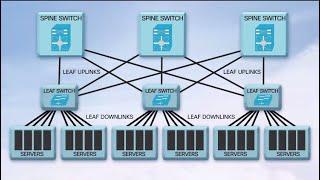
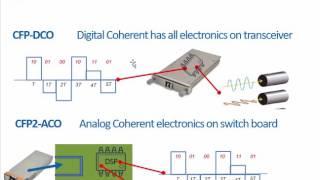
IT security is the protection of computer systems from theft of or damage to their hardware, software or electronic data, as well as from disruption or misdirection of the services they provide.
Cybersecurity includes controlling physical access to system hardware, as well as protecting against harm that may be done via network access, malicious data and code injection.[1] Also, due to malpractice by operators, whether intentional or accidental, IT security personnel are susceptible to being tricked into deviating from secure procedures through various methods of social engineering.[2]
The field is of growing importance due to increasing reliance on computer systems, the Internet[3] and wireless networks such as Bluetooth and Wi-Fi, and due to the growth of "smart" devices, including smartphones, televisions and the various tiny devices that constitute the Internet of Things.
⭐ Important Links and Notes ⭐
⌨️ The creator of this course is Google ( Team: Grow with Google )
⌨️ As per Coursera FAQ section of Google IT Support Professional Certificate:
Yes, the content in the Google IT Support Professional Certificate is licensed under a Creative Commons Attribution 4.0 International License.
⌨️ For earning certificate, quizzes and supplementary reading please enroll for this course here: https://www.coursera.org/learn/it-security
⭐ Join Us ⭐
Email for any enquiry: geekslesson@gmail.com
Join our FB Group: https://www.facebook.com/groups/cslesson
Like our FB Page: https://www.facebook.com/cslesson/
Website: https://cslesson.org
⭐ Related Tags ⭐
Principle of IT security course
Complete IT security course from google
cyber security course in
cyber security course online
cyber security course syllabus
cyber security course pdf
cyber security courses
cyber security training for beginners
cyber security course fees
best cyber security courses online
Cybersecurity includes controlling physical access to system hardware, as well as protecting against harm that may be done via network access, malicious data and code injection.[1] Also, due to malpractice by operators, whether intentional or accidental, IT security personnel are susceptible to being tricked into deviating from secure procedures through various methods of social engineering.[2]
The field is of growing importance due to increasing reliance on computer systems, the Internet[3] and wireless networks such as Bluetooth and Wi-Fi, and due to the growth of "smart" devices, including smartphones, televisions and the various tiny devices that constitute the Internet of Things.
⭐ Important Links and Notes ⭐
⌨️ The creator of this course is Google ( Team: Grow with Google )
⌨️ As per Coursera FAQ section of Google IT Support Professional Certificate:
Yes, the content in the Google IT Support Professional Certificate is licensed under a Creative Commons Attribution 4.0 International License.
⌨️ For earning certificate, quizzes and supplementary reading please enroll for this course here: https://www.coursera.org/learn/it-security
⭐ Join Us ⭐
Email for any enquiry: geekslesson@gmail.com
Join our FB Group: https://www.facebook.com/groups/cslesson
Like our FB Page: https://www.facebook.com/cslesson/
Website: https://cslesson.org
⭐ Related Tags ⭐
Principle of IT security course
Complete IT security course from google
cyber security course in
cyber security course online
cyber security course syllabus
cyber security course pdf
cyber security courses
cyber security training for beginners
cyber security course fees
best cyber security courses online
- Category
- Tech Education Channel
Be the first to comment