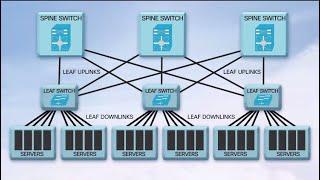
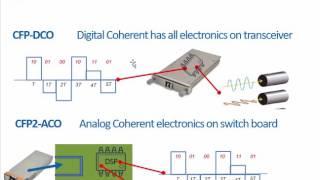
Network and cybersecurity consist of practice and policies to prevent unauthorized access to network or misuse or modification of computer network.
Network and cybersecurity work on both public and private network.
Network and Cybersecurity revolve around authenticating users and only allowing the real user to access data for which the data is made for.
Network security covers the variety of computer network both public and private
Network security starts with authenticating just one detail i.e. username +password is termed as one-factor authentication
in the network and cybersecurity in two-factor authentication, something that user "has" is also used like OTP, mobile number
Network and cyber security also have three-factor authentication which is something that user "is" is used eh fingerprint
In network and cyber security communication between two hosts using a network may be encrypted to maintain privacy
In network and cybersecurity, honeypots are used i.e. event meant as a distraction can be deployed in the network as early-warning tools, honeypots encourage attackers to spend their time and energy on decoy server while distracting their attention on real server
Network and cybersecurity work on both public and private network.
Network and Cybersecurity revolve around authenticating users and only allowing the real user to access data for which the data is made for.
Network security covers the variety of computer network both public and private
Network security starts with authenticating just one detail i.e. username +password is termed as one-factor authentication
in the network and cybersecurity in two-factor authentication, something that user "has" is also used like OTP, mobile number
Network and cyber security also have three-factor authentication which is something that user "is" is used eh fingerprint
In network and cyber security communication between two hosts using a network may be encrypted to maintain privacy
In network and cybersecurity, honeypots are used i.e. event meant as a distraction can be deployed in the network as early-warning tools, honeypots encourage attackers to spend their time and energy on decoy server while distracting their attention on real server
- Category
- Tech Education Channel
Be the first to comment